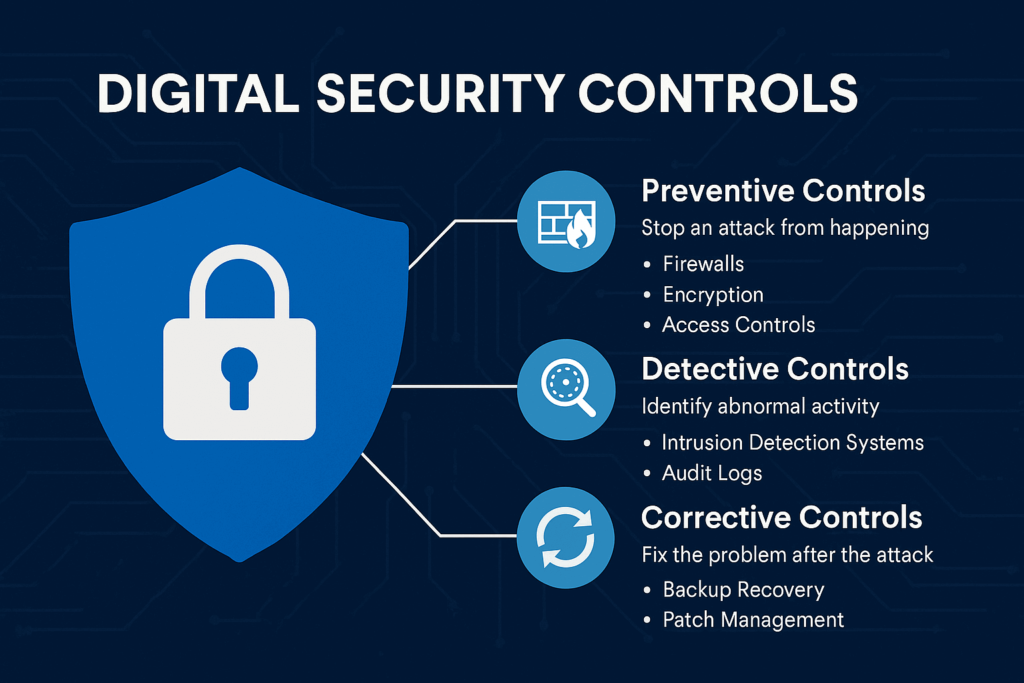
Digital security controls are guidelines or policies, as well as the physical hardware and software that protect your information, computers, and networks from unauthorized access, modification, and destruction. Think of them as your cyber bodyguards—always alert, and perpetually working undercover.
Cybersecurity controls are categorized into the following.
- Preventive Controls: Stop an attack from happening with the use of firewalls, encryption, and access controls.
- Detective Controls: Identify abnormal activity through intrusion detection systems and audit logs.
- Corrective Controls: Fix the problem after the attack with backup recovery and patch management.
The Importance of Digital Security Controls
Today, cyber threats are more relentless than ever. From ransomware attacks to data breaches, no organization or individual is immune. That’s where digital security controls come in—your first line of defense from unauthorized access, manipulation, and destruction of data.
Think of them as cyber bodyguards: always alert, always undercover, and working round the clock to protect your information, devices, and networks.
Read more in our New article: Data Science in Defense: The Hidden Power Behind Modern Cybersecurity
Digital Security Controls: What on Earth They are

At its essence, digital security controls are measures (policies, technologies, and processes) organizations implement to safeguard systems, networks, and information. But if you’re here, my guess is you’re not seeking a general definition — you need the correct source.
These are the main authoritative pages where you will find official definitions:
NIST Security Controls (U.S. National Institute of Standards and Technology)
👉 NIST SP 800-53: Security and Privacy ControlsISO/IEC 27001 (International Standard for Information Security Management)
👉 ISO.org – ISO/IEC 27001 Information SecurityCIS Critical Security Controls (Center for Internet Security)
👉 CISecurity.org – CIS Controls
Each of these resources provides a structured catalog of digital security controls — whether you’re working in government, enterprise, or small business IT.
Types of Digital Security Controls
If your search intent is specifically to find the categories of controls (because you’ve probably seen the terms “preventive, detective, corrective”), here’s a quick navigation breakdown with references:
Preventive Controls – Stop incidents before they happen.
Examples: firewalls, access restrictions, encryption.
Where to read more: CISA.gov – Cybersecurity Best Practices
Detective Controls – Identify and alert about incidents.
Examples: log monitoring, intrusion detection systems (IDS).
Where to read more: CISecurity.org – Controls 8: Audit Log Management
Corrective Controls – Respond and recover after incidents.
Examples: backups, patching, recovery plans.
Where to read more: NIST.gov – Incident Response Guidelines
If you’re navigating for a visual reference, the CIS Controls page has a handy list of categorized controls that’s widely used across industries.
Where to Learn About Security Controls for Businesses
If your intent is to find business-focused security guidance, the following are the most direct sources:
Small Businesses → FTC Small Business Security Portal
Enterprise Security → Gartner Security & Risk Management Insights
Compliance Standards → HIPAA.gov Security Rule
These sites are where you’ll land if you’re specifically searching for digital security controls by business type or industry.
Key Elements of Effective Digital Security Controls
When people search for this section of the guide, they’re usually hoping for a checklist or framework reference. Good news: you don’t need to create it from scratch. Here’s where to look:
Access Control Mechanisms
👉 NIST Digital Identity Guidelines
Covers multi-factor authentication (MFA), password policies, and identity management.Authentication & Identity Management
👉 Okta.com – Identity & Access Management
(Vendor-based but excellent for practical deployment guidance.)Encryption & Data Protection
👉 Cloud Security Alliance Encryption Guidelines
Covers how encryption should be applied in cloud and hybrid environments.Monitoring & Logging
👉 CIS Control 8 – Audit Log Management
If your navigational purpose is to bookmark the proper sources, these are the “must-stop” sites for deploying strong security controls.
Network Security Controls
When individuals specifically look for network security controls, they most likely desire action-oriented links to the tools, standards, and guides that establish best practice. Rather than an overall overview, here’s where you need to go:
Firewalls & Intrusion Prevention
👉 CISA – Firewalls Explained
👉 Palo Alto Networks – Intrusion Prevention SystemsVPNs & Remote Access Security
👉 NIST Guidelines for Telework & Remote Access (SP 800-46r2)
👉 Cisco VPN Solutions OverviewNetwork Monitoring & Threat Intelligence
👉 CIS Control 13 – Network Monitoring & Defense
👉 IBM X-Force Threat Intelligence
If you’re looking to find particular solutions, frameworks, or federal guidelines on network security controls, these links will direct you to the authoritative places without having to bounce between several blogs.
If you enjoyed learning about digital security controls, you might also love these related reads: Oasis Artificial Intelligence: How AI Is Shaping the Future of Security
Application Security Controls
Application-level attacks are among the most prevalent threats, and a lot of searchers seeking this page wish to jump straight into guides on secure development and application defense.
Here are the straight links you ought to bookmark:
Secure Coding Practices
👉 OWASP Secure Coding Practices Guide
This is the gold standard for developers and security engineers.Web Application Firewalls (WAFs)
👉 AWS WAF Overview
👉 Cloudflare WAF DocumentationPatch & Vulnerability Management
👉 NIST Vulnerability Management Guide (SP 800-40 Rev. 4)
👉 US-CERT Vulnerability Notes Database
Cloud Security Controls
It seems most folks typing “cloud security” into their search engines looking for specific security standards for the cloud. For those not looking for generic or ambiguous recommendations here are the recommended resources:
Shared Responsibility Model (AWS, Azure, GCP)
👉 AWS Shared Responsibility Model
👉 Microsoft Azure Shared ResponsibilityCloud Data Encryption
👉 Google Cloud Encryption Documentation
👉 CSA (Cloud Security Alliance) Encryption GuideCloud Monitoring & Compliance
👉 Cloud Security Alliance – STAR Registry
👉 NIST Cloud Computing Security Guidelines
Emerging Trends in Digital Security Controls
If you searched for “digital security control future” or “current cybersecurity trends,” you want authoritative perspectives on the next big thing. Here are the places to look:
AI & Machine Learning in Security
👉 MITRE AI & Security Research
👉 IBM AI in CybersecurityZero Trust Architecture
👉 CISA Zero Trust Maturity Model
👉 NIST Zero Trust Architecture (SP 800-207)Blockchain for Security
👉 World Economic Forum – Blockchain Security
Physical Security Controls in the Digital Era
As SaaS apps are provided over the internet, users have the option to access them from practically anywhere with a reliable connection to the web and a suitable device.
Biometric Access Control
👉 Biometric Update – Industry News & Guides
👉 NIST Biometric StandardsCCTV & Surveillance Standards
👉 ASIS International – Physical Security StandardsData Center Security
👉 Uptime Institute Data Center Security Resources
👉 Google Data Center Security Tour
Governance, Risk, and Compliance (GRC) in Security Controls
GRC? (Governance, Risk, and Compliance). Sounded like corporate speak, didn’t it? But let me tell you: without it, your security program is effectively a car with no steering wheel.
Governance = rules of the road.
Risk Management = seeing potholes before you drive into them.
Compliance = ensuring that you’re not violating traffic laws.
All together, they prevent your business from driving off into a cybersecurity cul-de-sac. Believe me, auditors are thrilled when you do this.
Humans: The Strongest Link (and the Weakest One Too)
Most cyberattacks are successful not because they are well-planned but because people are careless. Your staff can be your greatest asset, or they can put you at the greatest risk.
This is why security awareness training is not just a formality. Simple measures like phishing simulations, brief training tutorials, and “Hey, don’t click that!” posters can be very effective.
A reminder: a hacker doesn’t have to break down your firewall if Jim in accounting is careless and gives them the access they need.
Incident Response: Your “Oh No” Game Plan
Bad news: no system is 100% bulletproof. Good news: if you’ve got an incident response plan, you won’t be running around like headless chickens when things go south.
Think of it like a fire drill:
Prepare – Assign roles. (Who calls IT? Who tells the boss?)
Detect – Spot the smoke before the whole house burns.
Contain – Shut the doors, stop the spread.
Fix & Recover – Get systems back online.
Learn – Patch the hole so it doesn’t happen again.
Companies that practice this bounce back faster. Those that don’t… end up on the news.
Are Your Security Controls Actually Working??
You wouldn’t keep paying for a gym membership if you never saw results, right? Same deal with cybersecurity controls. You need to measure them.
Some quick “fitness trackers” for your security:
MTTD (Mean Time to Detect): How fast do you spot trouble?
MTTR (Mean Time to Respond): How fast do you fix it?
Patch Compliance: Are your updates on time, or months late?
Blocked Intrusions: Proof your defenses are actually doing something.
Phishing Test Results: How many people still fall for “You’ve won a free iPhone”?
If the numbers don’t look good… time to hit the cyber-gym.
Conclusion: Building a Strong Digital Shield
Digital security controls are no longer optional—they’re the foundation of safe business operations.
Preventive, detective, and corrective measures work best together, as layers in a defense system. Whether you’re following NIST standards, ISO frameworks, or CIS best practices, the goal is the same: keep attackers out and keep your data safe.
Remember: cybersecurity is not a project that you ever complete—it’s a journey. Through the right combination of policies, technologies, and human awareness, you don’t build defenses, you build resilience.